
The WannaCry attack has put the security of many companies into question. That is why many users are increasing that security. One way to increase that security is make use of a security key or a Security USB. This mechanism allows the user to use the Windows computer as long as the security USB is connected to the computer.
It is a good security method because we will only need a blank USB to make the equipment work. And in return we can limit computer access to users who are not welcome to do so.
Along with the USB, we will need the USB Raptor program. This program is free and we can download it from this link. Once downloaded, we have to connect the usb to the computer and then run the installer. Once we have installed USB Raptor, we run it.
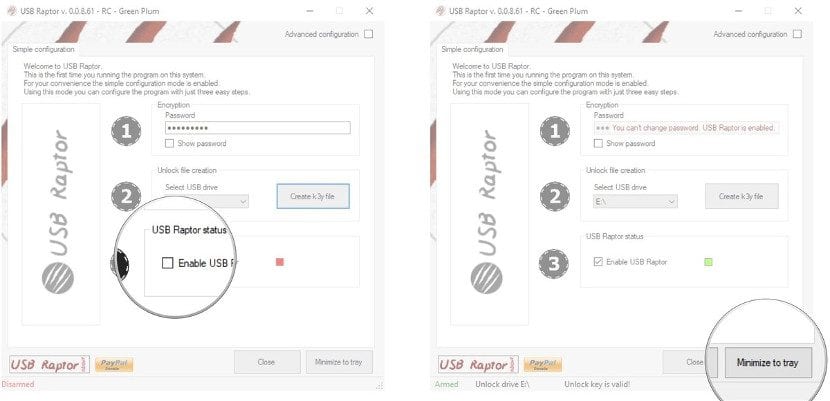
In the USB Raptor screen we have to first create the USB with the k3y file. For this we write a password (very important keep it off the computer because if we forget it we can have serious problems). Then we select the unit where the USB is and press on the button to create K3y FileAll this will allow the program to recognize the security USB and not another USB. Once created, at the bottom we find an option called "Enable USB Raptor".
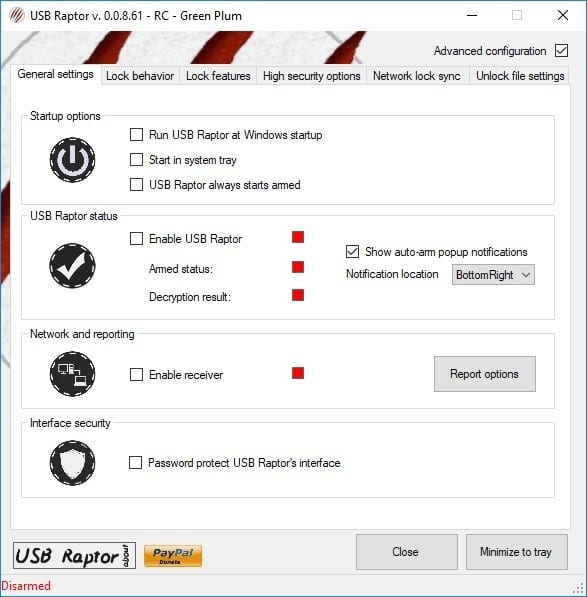
By checking it, we activate the program and therefore the system will crash the moment we disconnect the USB from the computer. But before that, we have to go to the upper right where "Advanced Configuration" appears, click on it and several program options will appear. In this case we have to press the option "Run USB Raptor at Windows Startup". Thus, the program will be executed with the Windows login, so we will have to use the security USB for Windows to start the session. As you can see, it is an interesting and cheap security system, at least cheaper than a fingerprint and iris reader to access it Do not you think?