
It may be that there is someone who has managed to access our computer. In this way, said person could install programs on the computer, which could be malicious. One way to avoid this situation is to block the installation of programs from outside the Windows 10 store.. Thus, it is only possible to install those programs available in the store.
It is an option that gives us security. Because the programs that we have available in the Windows 10 store are all safe. So we have nothing to worry about in this regard. Here we show you how this is achieved.
Windows 10 has a native option that allows us to block the installation of programs that do not come from the store. So it is very easy to activate it, since we only have to look for the option itself. When we activate it, we will have greater protection on the computer.
We open the system configuration first. Therefore, we go to the start menu and click on the gear-shaped icon. Once inside, we have to go to the applications section. Click on it and a new window opens with this option.
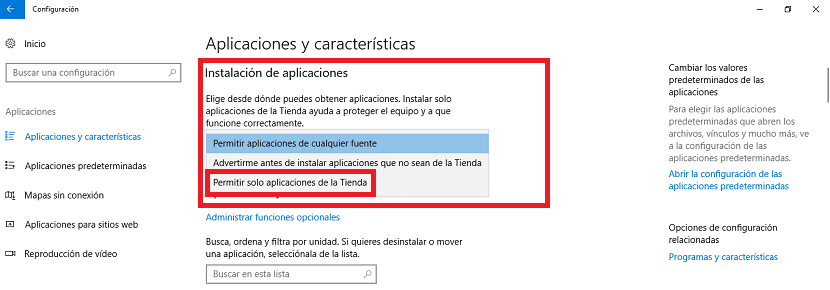
The first option that comes out is a section called application installation. We can see that in it we find a drop-down list with several options. One of them is allow only the installation of programs from the Windows 10 store. You can see in the image exactly its location.
Therefore, all we have to do is select this option. Once we have done this we can exit the configuration. In this way, when installing a program we will only be able to do it from the Windows 10 store. Thus, if someone tries to install a program on the computer, they will not be able to do it.
And if the one who is going to install a malicious program knows this, because I don't think there is much security, they should put the pin option when trying to change this option