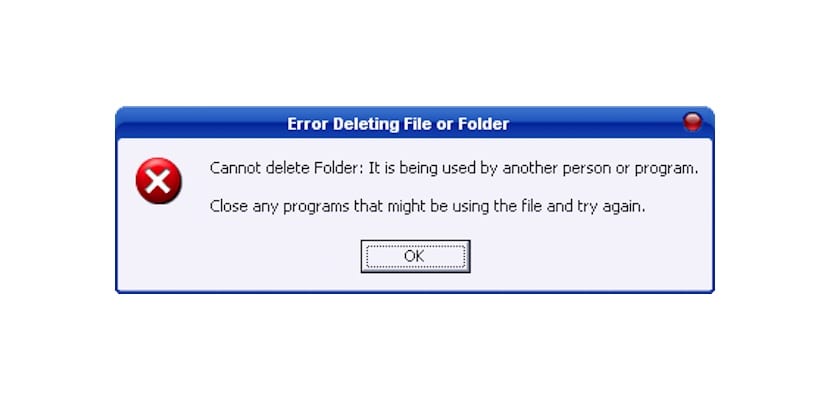
Depending on the use we make of our equipment, it is likely that on more than one occasion we have met with an application or file that does not want to leave our team and forces us to resort to third-party applications as long as we do not have the necessary knowledge.
Fortunately, as the years have passed, Windows has natively implemented an antivirus called Windows Defender, an antivirus that is responsible for analyzing any content that we want to install on our computer and in this way avoid unpleasant surprises like the one I comment on in this article.
If we want to delete any file that is installed on our computer but there is no way to do it in a traditional way, On the Internet we have at our disposal the Unlocker application, an application that has become a reference within Windows to be able to eliminate these types of files.
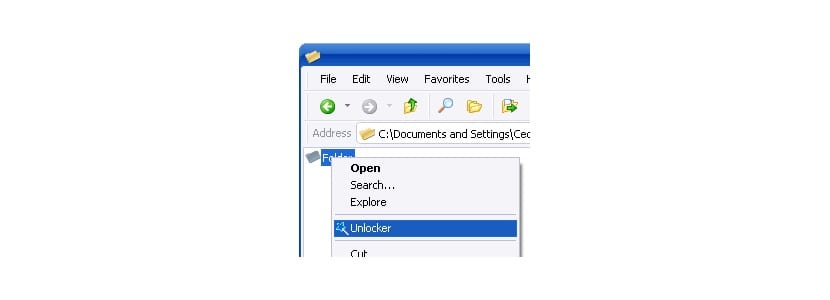
The operation of the application is very simple, since once we have installed it, we just have to hover the mouse over the file and select open with Unlocker. At that time, the application will perform all the necessary methods to be able to completely remove the file or files from our computer.
Sometimes, in order to eliminate any trace of the file in question, we must end up restarting the computer. Unlocker has no configuration options or any other function. This application is the one you are looking for if after restarting your computer several times, Windows keeps telling you that either you do not have permissions to delete it or the application is in use and cannot be eliminated at that moment.
Unlokcer will close all processes related to the file and unlink them from the system so that in this way it can be automatically eliminated by the application without us having to start in safe mode.