
In order to use certain online services, it is often necessary to create an account and log in. This is something that, in general, is fine by allowing the creation of a custom profile that you access later to see the data. However, especially in the case of those smaller services, it happens that sometimes data ends up being leaked due to security-related issues thereof.
And, specifically, this is not overly pleasant. if, for example, the same password has been used to access other third-party services, because by combining different techniques it is possible that someone ends up accessing private and confidential information that you may have stored in different online portals, being able to even access bank details so you have to be quite careful in this regard.
How can I tell if my passwords have been leaked due to a vulnerability?
In the first place, to know this it is important to clarify that nothing is infallible so It is possible that some of your accounts have been the victim of a security breach but nonetheless there is no information enough to determine it. Taking this into account, it is best to enter the associated email address in a service that checks for security flaws.
And in particular, one of the most useful and popular web pages is Have I Been Pwned. It is an online service in which you only have to enter an email address and it will check between different leaks that have taken place in recent years if your data appears in any list.
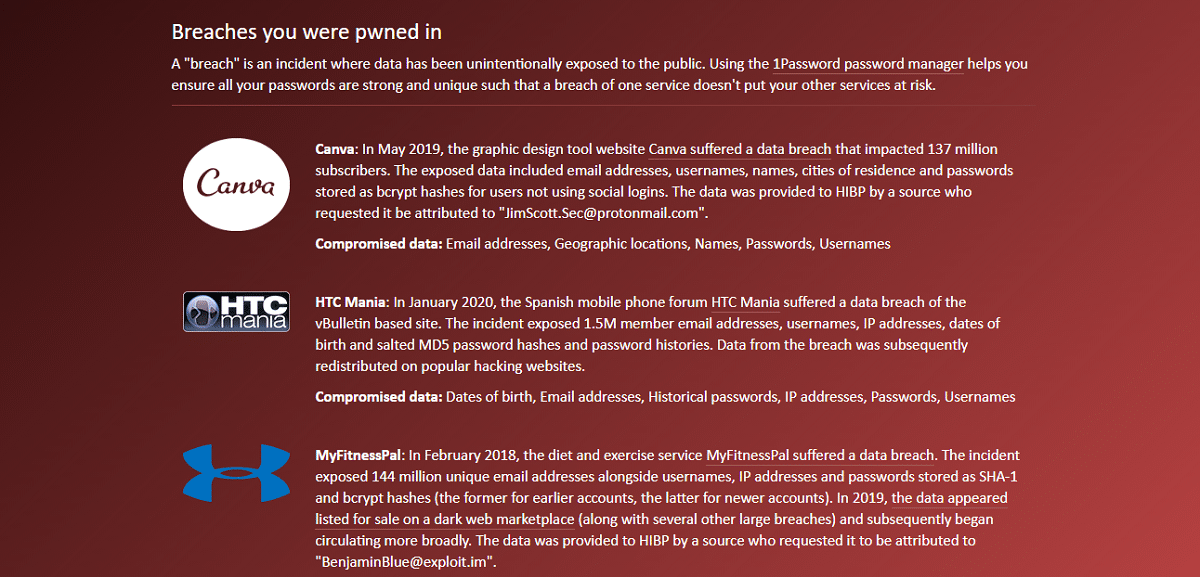

In the event that your email address has been leaked in a security breach, the service itself will show you where it appears within the sources it has indexed. If it appears in at least one, it is very important that you change the password within that service, as well as in any other in which you have used the same email and password combination, since otherwise your data could be in danger.